Introduction
The recent FortiOS / FortiProxy / FortiSwitchManager CVE has been reportedly exploited in the wild. We would like to provide additional insight into the vulnerability so users can begin to determine if they have been compromised. In this post we discuss enabling logging and IOCs for FortiOS 7.2.1. These steps will likely work on other vulnerable products, however we do not have other products configured in our lab for testing. See the details of our technical deep dive here.
Logging
If not already configured, REST API logging can be set through the Fortinet CLI with the following commands:
fortios_7_2_1 # config log setting fortios_7_2_1 (setting) # set rest-api-set enable fortios_7_2_1 (setting) # set rest-api-get enable fortios_7_2_1 (setting) # end fortios_7_2_1 #
IOCs
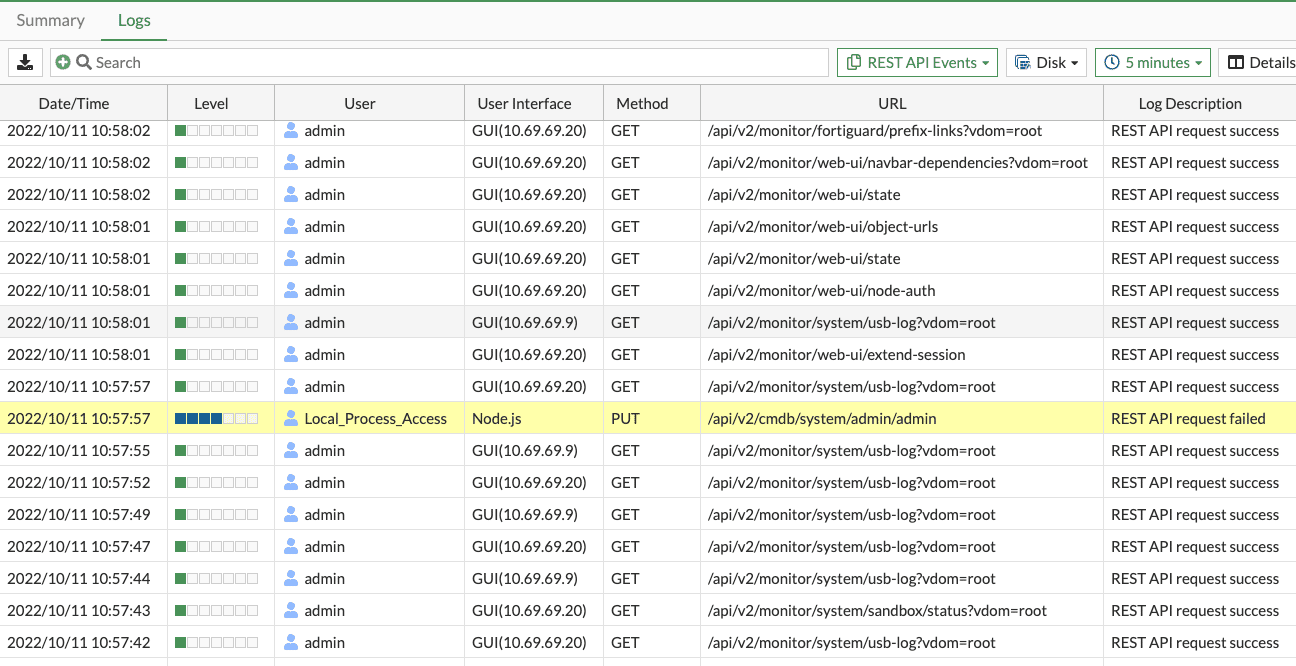
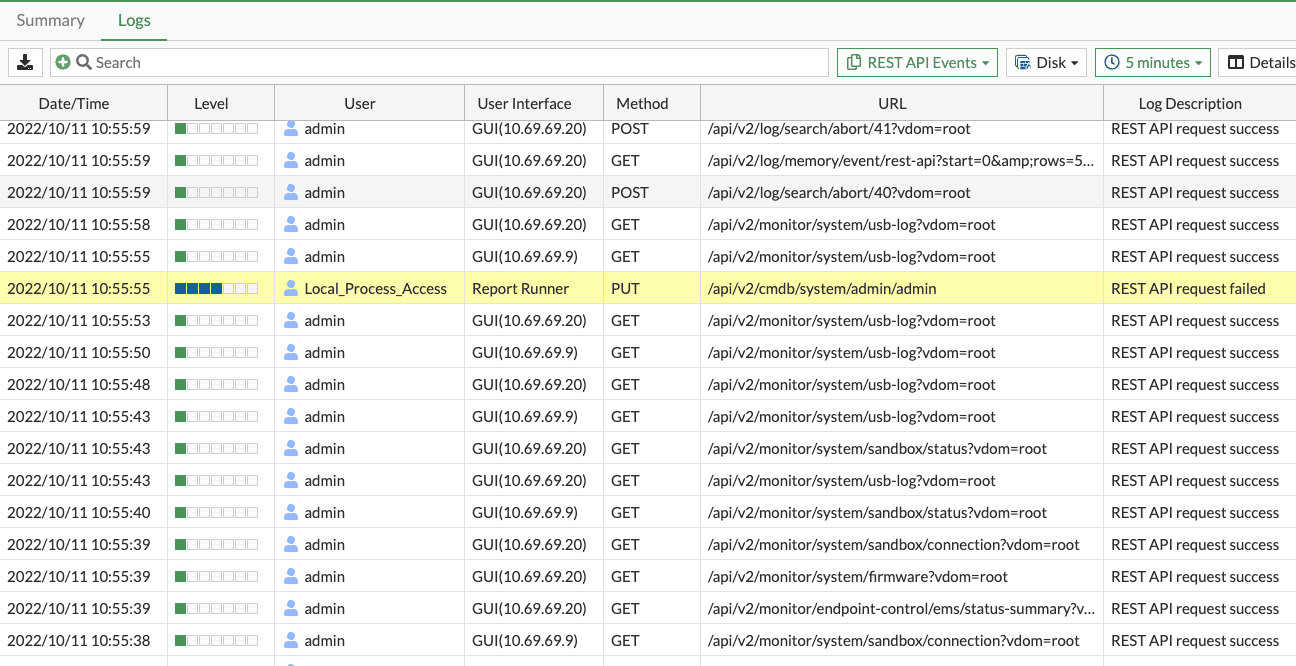
In addition to the recommendations by Fortinet to check the device’s log for user=”Local_Process_Access”, any affected system should also be checked for logs with user_interface=”Node.js” or user_interface=”Report Runner”. See the screenshots below for examples of the exploit running on our lab systems.
The exploit can be used with any HTTP method (GET, POST, PUT, DELETE, etc). Additionally, the REST API request failing is not an indication that an attacker was unsuccessful. In our lab environment, we were able to modify the admin users’ SSH keys though a REST API request that reportedly failed. We would also like to note that a system configured for production use may produce logs that match these IOCs naturally. However, we would not expect these IOCs to match with URLs targeting sensitive REST API endpoints.
Attacker Mindset
The collection /api/v2/ endpoints can be used to configure the system and modify the administrator user. Any logs found that meet the above conditions and also have a URL containing /api/v2/ should be cause for concern. Further investigation of any matching log entries can reveal any damage an attack has done. Additionally, an attacker may perform the following actions to further compromise a system:
- Modify the admin users’ SSH keys to enable the attacker to login to the compromised system.
- Add new local users.
- Update networking configurations to reroute traffic.
- Download the system configuration.
- Initiate packet captures to capture other sensitive system information.